19 Jan Setting up an OpenVPN server on Windows
A few years (!) ago, I wrote about using [accessing your files from anywhere](https://www.michaelcheng.us/stuff/15) using a custom DDNS setup. In the 2 years I've been in Chicago so far, my entire apartment building has shared one IP address. That meant my custom DDNS solution couldn't work anymore, and so I looked into other ways I could access my files from anywhere. I couldn't find any.
There are things like [ngrok](https://ngrok.com/) that can expose local servers through tunnels, but that wouldn't work for my on-demand use case where I'd remotely turn on my computer to access files through SMB.
I looked into getting a NAS such as [QNAP](http://qnap.com) or [Synology](http://synology.com) but decided the hassle and cost of setting up these storage devices wasn't worth it (versus the amount of times I'd actually need access to all my files).
I settled for the obvious solution of just copying all important files to my phone whenever I traveled for extended periods of time. That actually wasn't so bad. However, my building recently got switched to Comcast. I had mixed feelings about the change: there are lots of negative reviews about Comcast, and I never really did have any issues with Access Media 3 (despite the [horrible reviews](https://www.google.com/search?q=access+media+3&oq=access+media+3&aqs=chrome..69i57j0l5.2131j0j7&sourceid=chrome&ie=UTF-8#lrd=0x880e4c703b6c0ca3:0x70048713d7f9b61b,1,,,) it has).
The first thing I realized with the new Comcast service was that I had my own IP address again. That opened up many doors, including finally being able to again have on-demand access to all my files from anywhere. The first thing I did, however, was purchase a 3 year VPN service from [NordVPN](http://nordvpn.com). Having a real IP address again (as convenient as it is) sounds a bit scary.
The next thing I did was use my [CpanelDdns](https://github.com/mlcheng/php-CpanelDdns) library to dynamically set the [A record](https://support.dnsimple.com/articles/a-record/) of a domain to point to my IP address. I used my old Android phone (that I use as a clock) and [MacroDroid](https://play.google.com/store/apps/details?id=com.arlosoft.macrodroid) to setup the recurring HTTP request.
Next, I wanted at least remote access to my computer. Being able to turn it on was a nice first step. I set up a port forward to my computer and used Wake on LAN to send the magic packet.
With the computer turned on, I wanted VNC access. I set up a port forward to my computer and connected via 4G on my phone. When my screen appeared, I suddenly felt like something was fishy. I don't think VNC has any smart way of rate-limiting. I found "Expert" settings that could set a blacklist threshold.
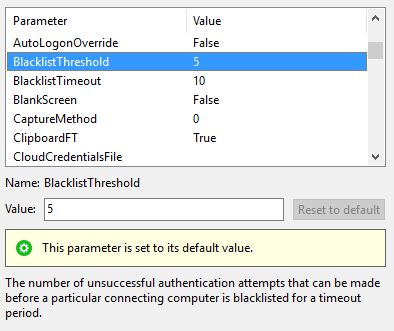
What that does is prevent the connecting client from re-authenticating if the password is wrong. I changed that to 1, and set the timeout to 600 seconds. That means anyone attempting to brute-force my password would only get one try, and they'd have to wait 10 minutes between each guess. I then found out that VNC [blacklists just the IP](https://help.realvnc.com/hc/en-us/articles/360003563111-Too-many-security-failures) when there is authentication failure. It seems like there's so many ways to just get around whatever VNC decides to blacklist. What I wanted was something like using a certificate to authenticate rather than using a password. Something like SSH. Turns out there [is a way](https://help.ubuntu.com/community/VNC?action=show&redirect=VNCOverSSH) to VNC over SSH. But that wouldn't work for my use case of connecting with my phone.
At this point, I realized what I really needed was a VPN server. A simple search for ["openvpn server windows"](http://www.lmgtfy.com/?q=openvpn+server+windows) doesn't really show too many useful resources. The first step is to just check out the [guide on Reddit](https://www.reddit.com/r/OpenVPN/comments/81q2q6/guide_how_to_set_up_openvpn_server_on_windows_10/) and the "official" [Easy Windows Guide](https://community.openvpn.net/openvpn/wiki/Easy_Windows_Guide). They're both somewhat similar, so either one will do. The trickiest part for me was finding out what settings I should keep and what I should change.
In order to route client traffic through the server, this setting must be enabled:
```
push "redirect-gateway def1 bypass-dhcp"
```
The simple warning "_(The OpenVPN server machine may need to NAT or bridge the TUN/TAP interface to the internet in order for this to work properly)_" is not one to be taken lightly, as I later found out.
Because the server is set to take _10.8.0.1_ for itself, it ended up being on a different subnet than other things on my network. I tried changing this to `192.168.1.0` but that had many issues so I gave up on that. I ended up using `push "route 192.168.1.0 255.255.255.0"` to allow clients to reach this subnet as well. I'm not sure if this does what I expect, but everything works now, so I'm keeping it.
There's nothing too special about the `client.ovpn` file that needs to be changed.
You **must** configure the Windows Firewall to allow incoming traffic through UDP to the port your VPN server is listening on.
If you set it all up and nothing is working and you have no idea where to start debugging (e.g. is it the port forward that broke, is it even running, etc), it's helpful to know that you can start the server without going through `services.msc`, with the help of:
```
$ openvpn ..\config\server.ovpn
```
When nothing was working at first, I checked the output of this command to find out I had authentication errors.
After figuring all that out, I had successfully connected my phone to my Windows OpenVPN server at this point. However, I couldn't access local SMB file shares. I found out that the OpenVPN TAP network was set to Public, where file sharing was turned off (as it should).
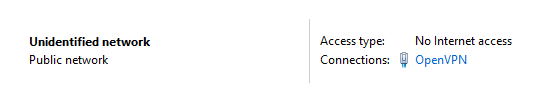
There are many ways to resolve this issue, but I ended up going with [this simple solution](https://superuser.com/a/791640) of setting the default gateway to the DHCP server address of the TAP network.
Surprisingly, I still had no access to the SMB share after doing this. I wondered if there were ACLs that only allowed access to file shares in the local subnet. There were.
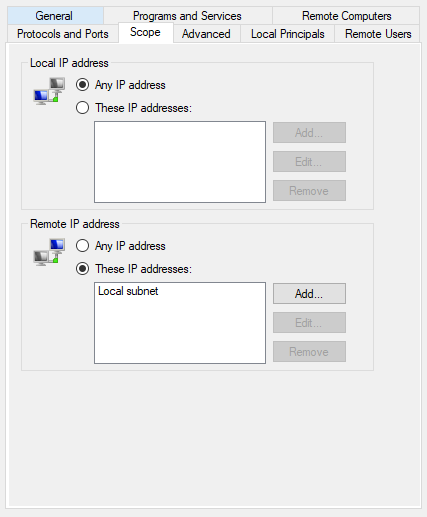
In the Windows Firewall, find `File and Printer Sharing (SMB-In)`. In the `Scope` tab, add the subnet set for VPN clients.
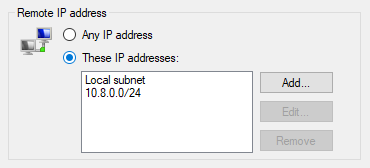
And there you have it. A HUGE caveat of this is I have **no idea how to get actual Internet traffic working** through this VPN. It seems like I can only access local resources, but that's no problem for me since I only want access to VNC and SMB. Maybe someday I'll figure out how this all works...
Comments
Nice work, Michael!
Thanks DD!! :)
Hi Michael, ツツ
Hi MM :)